本篇文章會使用 google public image: gcr.io/cloud-builders/gsutil,並用 bash -c 將 token 傳入 container。示範如何不安裝 google sdk 測試 gcp service account。
用 docker run -it --rm --entrypoint bash <image> 與 container 互動。
#docker #docker-tips #gcp #service-account #gcloud-auth #gcs
Preparation
- 從 GCP export service-account.json
- Docker
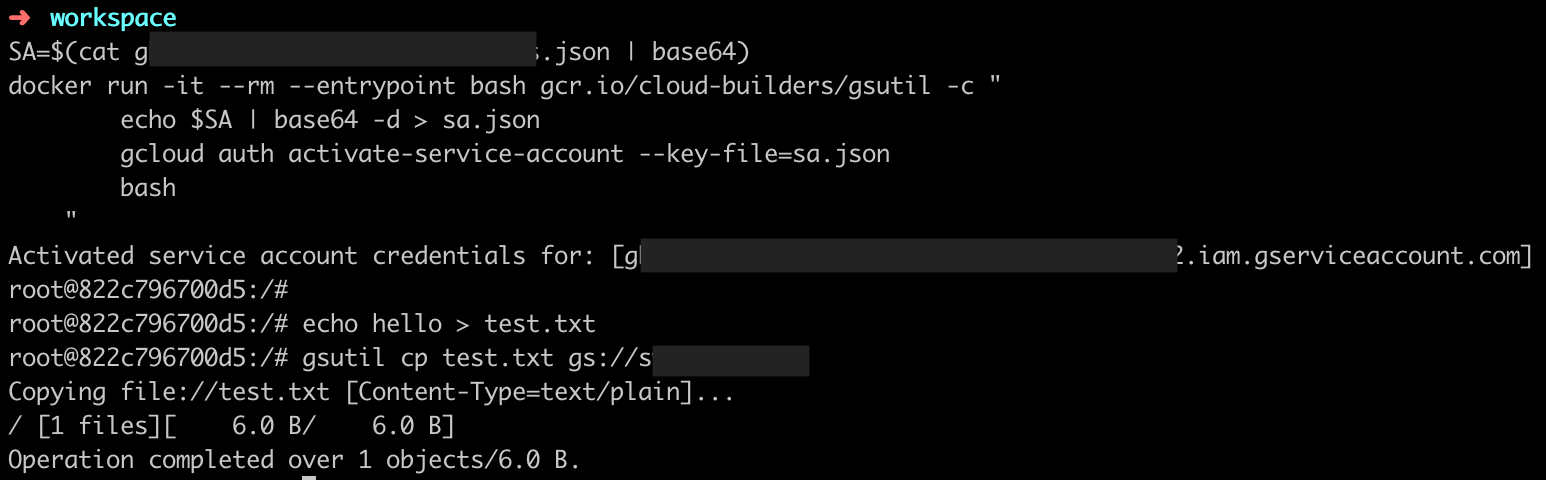
Let’s Go
SA=$(cat service-account.json | base64) |
用 gsutil 測試看看權限
echo hello > test.txt |
如果 service account 沒有 bucket permission:
AccessDeniedException: 403 xxxxx@xxxx.iam.gserviceaccount.com does not have storage.objects.create access to xxxxx.xxx/test.txt. |