After I create a EKS from AWS Console, I install external-secret using Helm. I pretty sure my IAM role and policy are correct. But I still can’t get secretsmanager. It turns out that it needs a IDP(Identity Provider).
ERROR, User: arn:aws:sts::xxx:assumed-role/test-cluster-NodeRole/i-0b5ab8adzzzf27a1b is not authorized to perform: secretsmanager:GetSecretValue on resource: sm_rammus because no identity-based policy allows the secretsmanager:GetSecretValue action |
I’m sure my IAM json is correct.
{ |
I found out that miss a us-east-1 IDP.
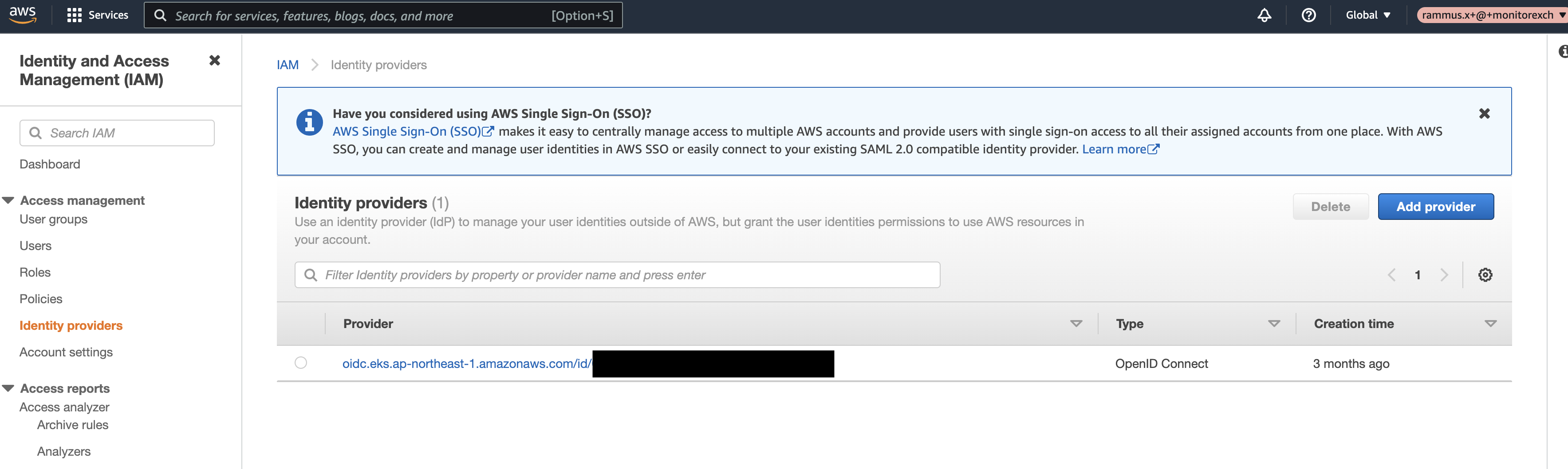
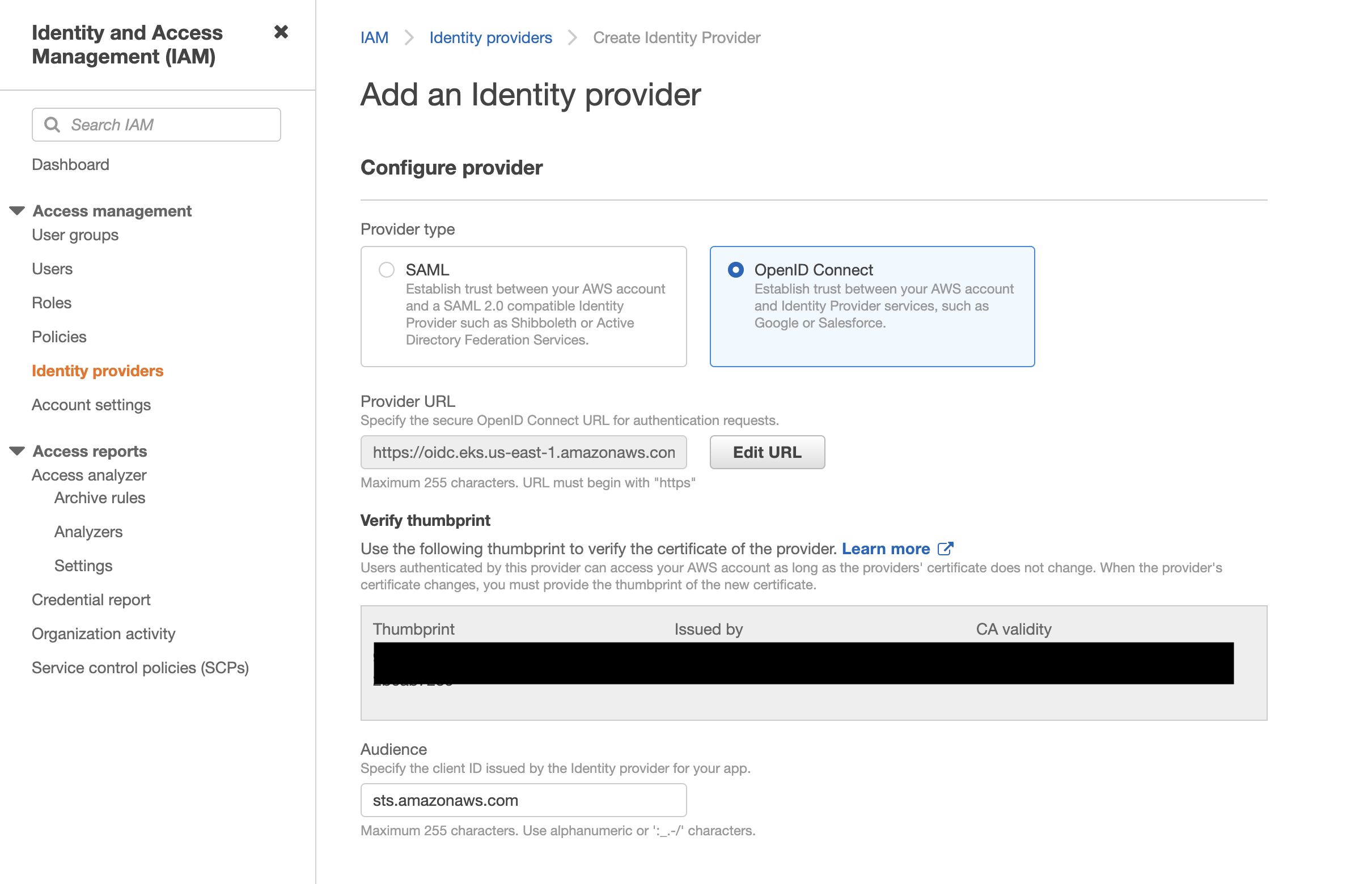
Create a new IDP, and fill:
- URL: Copy from EKSOpenID Connect provider URL
- Audience:
sts.awazonaws.com